There are many things to consider when virtualizing - storage requirements, number of users and disaster recovery to name a few. One thing that should be at the top of the list is security. Small businesses are embracing server, storage and other forms of virtualization as a means of reducing costs, improving efficiency and becoming more agile. The last post provides a framework for quantifying these benefits. What about the security of virtualization? Does introducing this new technology make small business IT infrastructure more vulnerable?
Some of the concerns around virtualization security really center around the bigger issue of IT sprawl. The notion is that since it is so easy to stand up new guest operating systems, security will suffer. This is a bit of a flawed premise, though, because security policy is relevant whether securing a virtual or a physical machine.
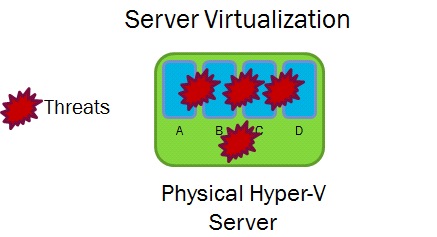
Other concerns center around the lag in traditional security control points, such as intrusion detection systems, support of virtual environments. Here are 5 ways to ensure that introducing virtualization does not impose security risks:
1. Conduct a security audit and vulnerability assessment:
Many small businesses do not have a good handle on how vulnerable their networks are - with or without virtualization. Information security is an entire domain on which there are many books published. That said, some high level things to consider are addressing perimeter security (e.g. firewalls, anti-virus, and anti-malware), information-centric security (e.g. identification of critical data, data loss, encryption, and authentication) as well as policy issues with personnel.
Security is a trade-off of cost, ease-of-use and risk. Armed with a thorough security assessment, small businesses may consciously make decisions about which information is the most critical to secure, how much they are willing to spend to protect it and what precautions they will require their end-users to take. This will be very helpful when considering what new security opportunities virtualization brings.
2. Fit technical controls to security policy rather than letting technical limitations dictate security policy:
If your security policy calls for patching and updating the operating system in a certain way, virtual instances of operating systems should be no different. The benefits of virtualization far outweigh the fact that you have to maintain one additional operating system than you did before. This, in fact, is not even a technical limitation - it is just something to bake into operational procedures. If there are perceived technical security limitations with virtualization, one can always address these through the traditional framework of cost, ease-of-use and risk. In this way, one can implement security policies consciously, rather than letting the "tail wag the dog", so to speak. If you are outsourcing your IT services, your provider should handle all operating system patches and updates seamlessly.
3. Make sure that you are up to date on the latest security products available:
Security vendors, like many others, are riding the hot wave of virtualization. Symantec and McAfee, among others, have full solutions focused on the security requirements of virtual environments:
Symantec's Virtualization Offering
McAfee's Virtualization Offering
So, the notion that intrusion detection systems or other security products are not able to support virtual environments is simply outdated in many cases.
4. Take an information-centric approach:
Virtualization further underscores the importance of moving from a perimeter-centric to an information-centric approach to security. A set of VHD files, the software snapshot of a virtual server, contain all of the information on that server. Protecting these files is critical. Both physical and logical controls should be implemented in order to prevent unauthorized access. There are plenty of controls available including multi-factor authentication, authorization and encryption. Again, it comes back to weighing the cost/ease-of-use/risk tradeoffs to come up with the right balance.
5. Ensure that virtual machine to virtual machine communications are secure:
This is a bit of a subset of number 3, but it is an issue that is raised prominently enough (e.g. Six common virtualization security risks and how to combat them), that it merits separate discussion. In fact, this problem has been solved. One company that offers a solution is called Vyatta. By placing a virtual firewall and virtual router on top of the Hypervisor, it is now possible to secure communications between virtual machines.
This blog is normally less technical, but I thought that it was important to highlight the fact that one, there are security concerns regarding virtualization and two, there are solutions. It is not so important to understand the details of those solutions, but to know that virtualization is worth the effort of implementing them.